Powershell scripts and cmdlets can be used to find failed Windows Updates on a local or remote computer. Powershell can collect all information about Windows Updates in log files. We can, then, analyze the log files to filter the failed updates.
We look at two ways by which we can find failed Windows Updates using Powershell below. The first approach will generate Windows Update logs and filter the log file for failed entries.
The second approach (thanks to Technet) is about using the WMI Object method to filter the log files and report failed updates in a summarized approach.
Find failed Windows Updates using Windows Update logs in Powershell
To find Windows Updates that may have failed on the system in Powershell, we will generate logs through the Powershell command.
Get-WindowsUpdateLog -verbose
The verbose command will generate all the Windows logs about the Windows Updates that may have been installed on the system. The command output may take time to generate on the console. The command output will be a really long one and the logs will stretch beyond a single console screen.
During the course of verbose log generation, all the log and ETL files are merged to create a single entity of logs for Windows Updates. The default verbose Windows Update log file is stored on the desktop as a WindowsUpdate.log file.
In my case, the default verbose Windows Update log file was generated and saved under C:\Users\HP\Desktop\WindowsUpdate.log.
Here is the command output that I got after running the Windows Update verbose command in Powershell.

When you run the Windows Update verbose command, you need to pay special attention to the last section of the command output. It is also called the ‘Output’ section of the command. You should see a summary of the Windows Update verbose log command in the output section to confirm if the Windows Update logs were successfully generated.
In the screenshot below, you can see the output section. It talks about the creation of a merged WindowsUpdate.log file successfully.

Once the WindowsUpdate.log file has been generated, we will run it through a filter to report all the lines in this log file with ‘Failed’ status.
Select-String -Path C:\Users\HP\Desktop\WindowsUpdate.log -Pattern ‘Failed’ | Select-Object -Last 10
The Select-String cmdlet will pull all those lines from the log file that match the pattern ‘Failed’. For ease of analysis, we have kept a limit of the last 10 pattern matches only. This means that the above cmdlet will go through the log file generated by the Windows Update verbose log command.
And, it will pull the last 10 occurrences of the ‘failed’ pattern in the Windows Update log file.
The output of this command is represented in the screenshot below.
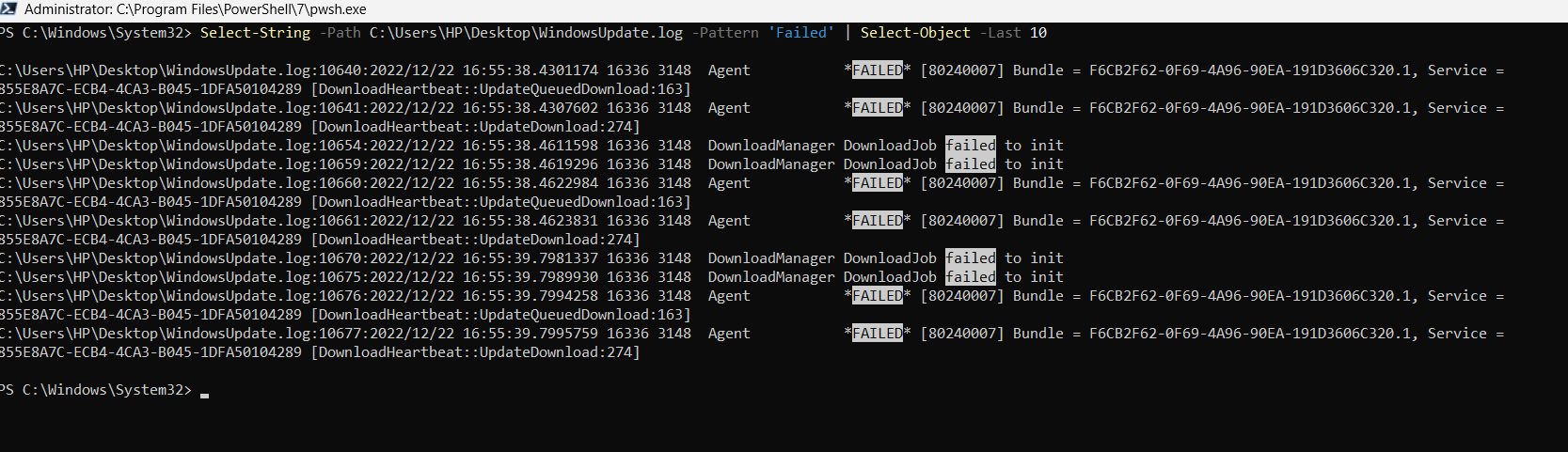
From the filtered output, you can see that the Windows Update failed with an error message [80240007].
Find failed Windows Updates using CIM Instance in Powershell
The CIM Instance method offers a concise way to filter the failed Windows Updates on a system. CIM Instance will work on the Win32_reliabilityrecords class to fetch the list of failed updates on a Windows computer.
The exact command to find the failed updates and display them on the console in a chronological way is given below.
get-ciminstance win32_reliabilityRecords -filter “sourcename = ‘Microsoft-Windows-WindowsUpdateClient'” |where { $_.message -match ‘failure’ } |select @{LABEL = “date”;EXPRESSION = {($_.timegenerated)}},@{LABEL = “failed update”; EXPRESSION = { $_.productname }}| FT -AutoSize –Wrap
You can add the above command or filter expression in a Powershell script. Or, you could execute it from the Powershell command prompt. The result of this command looks like the screenshot below.

You can see from the command output that the last few failed Windows Updates are listed with the details of the update and the date on which the update failed.
Find failed Windows updates using WMI Object in Powershell
Like the CIM Instance method, WMI Object also uses the Win32_reliabilityrecords to find the updates that may have failed. The exact command is shared below:
get-wmiobject win32_reliabilityRecords -filter “sourcename = ‘Microsoft-Windows-WindowsUpdateClient'” |where { $_.message -match ‘failure’ } |select timegenerated, @{LABEL = “failed update”; EXPRESSION = { $_.productname }}| FT -AutoSize –Wrap
The output of this command is similar to the output from the CIM Instance method.
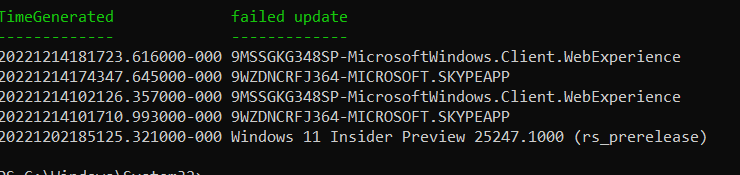
The failed updates are listed alongside the property of ‘timegenerated’. You can use the ConverttoDatetime function to convert time generated into the standard Date format.
Summary
In this Powershell tutorial, we saw three different ways by which we can find the failed Windows Update on a computer. The approach which uses the Windows Update log files has granular level detail. If possible, we should try to use the log files for the Windows Update.
Suggested Powershell Tutorials
You may like to read more Powershell tutorials for Windows computers. The following tutorials help in performing various system administration tasks on a Windows computer.
- How to find disk block size in Powershell?
- How to list installed printers in Powershell?
- How to find current directory path in Powershell?
- How do I convert epoch time to date in Powershell?
- How to find the public IP address using Powershell?
- How to find the boot directory using Powershell?
- How to find DoH DNS Servers using Powershell?
- How to get sid from the user account in Powershell?
- How to get system boot time in Powershell?
- How to append to a file in Powershell?
Rajesh Dhawan is a technology professional who loves to write about Cyber-security events and stories, Cloud computing and Microsoft technologies. He loves to break complex problems into manageable chunks of meaningful information.